- Get link
- X
- Other Apps
Blogs
- Get link
- X
- Other Apps
Suspicious Email
Todays blog will be a very short introductory incident response write up. A change, looking at the defensive side to security. Some background; we have been forwarded a spear-phishing email from an employee at the bank in which we work at. Our task is to find out relevant information about the suspicious email.
This is a lab from Immersivelabs.
We will be looking for several Indicators Of Compromise (IOCs) that can identify malicious behaviour on a system or network. We have the email saved in our working directory as a .msg file.
When we cat the file in terminal, we get a lot of data which looks a bit overwhelming.
Fortunately there are tools such as Oletools which can be used to forensically analyse this email message. However, I still need some time to get to grips with the tools and they were not absolutely necessary for this task.Task 1
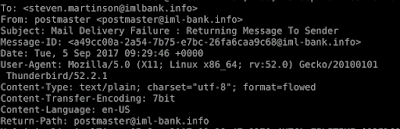
We have to identify what the malicious actor's mail server IP address is. We identify it as 54.214.177.125. We can identify this from the highlighted line during SPF checks. In Task 2 I will walk you through another way to identify the IP address of the mail server.
Task 2
We have to identify the malicious actor's fully qualified domain name in the email, this is just the full domain name for a host on the internet. We can identify this as mail.iml-bank.info as this is the FQDN of the malicious actors mail server. When we read the SMTP headers, we read them from bottom to top, the received header forms a trail of the mail servers that the email travelled through to reach its destination. The bottom (last) received header is where the email originated from, which identifies the FQDN of the malicious actors mail server and its IP address.
Task 3
We now need to find the malicious actors email address. We can identify this from the 'from' header as postmaster@iml-bank.info.
What did we learn and what can we do?
From the information we gathered, we now know the FQDN and the IP address of the malicious actors mail server, we can confirm where the email originated from and that it is indeed malicious. If we see an x-originating-ip header, we can do an IP lookup to identify the exact location of the IP address that the email came from.
We also take note of the email format, a legitimate domain name would be imlbank.info however the fake email the malicious actor used was iml-bank.info. We could block the senders email and IP address to prevent them from sending us further emails.
Additionally when reviewing the IP headers, we would want to look out for anything that looks weird such as a Gmail account being sent over a non Gmail SMTP server.
We would want to also inspect any attachments and links in the email also to ensure they are not malicious.
- Get link
- X
- Other Apps
Comments




You're a life saver.
ReplyDeletehello, can you please try Immersive Labs "Exfiltration Over Alternative Protocol" I am stuck on the last question and cannot seem to get the right answer
ReplyDelete