- Get link
- X
- Other Apps
Blogs
- Get link
- X
- Other Apps
Blaster
This is my third blog post on my OSCP journey and I will be walking through my methodology for this room (Blaster). This room is on the list of OSCP like machines published by TJnull. Although it wasn't too challenging, it did teach me a new Privilege Escalation technique.
An easy level CTF style challenge
Approx. 20 mins to complete
Target Enumeration
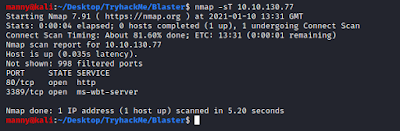
We will start off with a few Nmap scans to determine what ports are open on this machine.
Nmap -sT 10.10.130.77
- -sT for a TCP Connect scan
We notice that two ports are open; 80 hosting a webserver and port 3389 which is used for remote desktop (RDP).
I ran another scan to check the top 20 ports to make sure I didn't miss anything.
Nmap -sT -A --top-ports=20 10.10.130.77
- --top-ports=20 to scan the top 20 most common ports
We see that the two open ports are just 80 and 3389 as we suspected. We also get an indication that the operating system is Windows.
RDP Enumeration
The RDP protocol allows users access to the desktop on a remote host. The above snippet shows us information about the target and the RDP version, but nothing too interesting.
HTTP Enumeration
The Nmap snippet shows us that Microsoft-IIS is running on port 80
I used Curl to transfer data from the webserver to my machine.
curl -i http://10.10.130.77
- -i to include the http response headers in the output
We get a 200 OK back and some server information but nothing else too interesting.
Gobuster dir -u http://10.10.130.77 -w /usr/share/wordlists/seclists/Discovery/web-content/discovery-list.txt
It looks like a blog?
We notice that the author is wade. This could be a potential user of the machine we want to attack, lets remember that name.
After some enumeration of the website, we see a strange comment which seems to be a password.
I kept this password to a side and tried to enumerate further but could not find anything else that would be of use.
What do we know so far?
We know there are two ports open 3389 (RDP) and 80 (http). We have not found much but we have what could be a password for a potential user called wade. Since we have RDP open and we are hinted to use RDP by the challenge. We might be able to log in to get user access to the machine. Lets try it!
Exploitation methodology
I used Reminna (an RDP client) to log into the machine using the username Wade and the password we found and it worked!
I carried out some brief information gathering to find out information about the user we are.
The first interesting thing we see is that we have SeChangeNotifyPrivilege set to enable which means that we have granted the Bypass Traverse Checking user right. We essentially can bypass certain security checks and traverse the file system even if we dont have permissions of that traversed file system or directory.
We also see that we are not part of any interesting groups apart from the RDP users group.
We do however notice something interesting on the desktop.
When we google the name of the executable, we realise it is related to CVE-2019-1388. Maybe the user of the computer was researching the exploit and did not clean up very well. This exploit is for a Privilege Escalation vulnerability in the Windows Certificate Dialog.
Time to exploit this vulnerability which was demonstrated here:
First we confirm we are an unprivileged user on the machine
We see we are the user Wade.
We then run the executable from the desktop as an administrator.
Its asking for an administrator password, we do not know this so we will click show more information which will take us to the publishers site.
We dont see anything here, but we can try to save the page, at which point we will be prompted with an error message
We ignore the error message and will search for the system32 folder:
Now we will search for the CMD application:
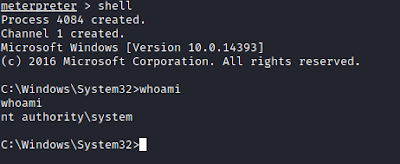
When we find it, right click on it and open it:
Congratulations - We now have a system Level CMD prompt!
Post Exploitation
We could do some post exploitation activities if we wanted to get a reverse shell from this system and possibly set up persistence for a more stable reverse shell.
Open Metasploit (msfconsole -q)
Set the payload to windows/meterpreter/reverse_http
Set our port and IP address to connect back to
use Run -j to run the exploit as a background job
Metasploit has now generated a PowerShell script with a Base64 encoded reverse-shell for us.
We can copy and paste this PowerShell script into our system level CMD prompt to catch a reverse shell in Metasploit.
Congratulations we now have a System level reverse shell. The last step would be to set up persistence and carry out post exploitation enumeration to gather any interesting files from the machine. We can also use run persistence -x to set up persistence when the system reboots.
Congratulations, we have finished the challenge. I will let you find the flags on your own.
I hope I explained my method clearly and provided justified reasoning for the actions I took. If you would like to try this room yourself, go here! If you have any feedback, I would love to hear it as I want to keep improving.
- Get link
- X
- Other Apps






















Comments
Post a Comment